Why multi-tenant workspaces demand a new approach to cybersecurity

Table of Contents
Multi-tenant. Shared. Flexible. These types of workspaces are becoming the norm. In these environments, multiple businesses—from startups to Fortune 500s—operate side-by-side under the same roof. But with this shift comes new risks, especially when it comes to cybersecurity.
In the traditional office setup, a single tenant would occupy an entire building or floor, and security was straightforward: You secured the perimeter, monitored who entered, and segmented the network as needed. However, in multi-tenant spaces, the dynamics are very different. Multiple tenants share the same infrastructure—often including the WiFi network—so the traditional security model no longer applies.
The new cybersecurity challenge in multi-tenant workspaces
As the operator of a multi-tenant workspace, you’re no longer just responsible for providing desks and meeting rooms. In many cases, you’re also responsible for providing the network, and that network must accommodate not only your tenants but also visitors, guests, and even day-pass users who need temporary access. The more people, devices, and companies using the same network, the more complex and vulnerable your environment becomes.
With bad actors constantly probing for weaknesses, cybersecurity can’t be an afterthought. The stakes are simply too high.
Comparing traditional offices vs. multi-tenant workspaces
To understand why multi-tenant workspaces require greater emphasis on cybersecurity, let’s compare them to traditional office environments:
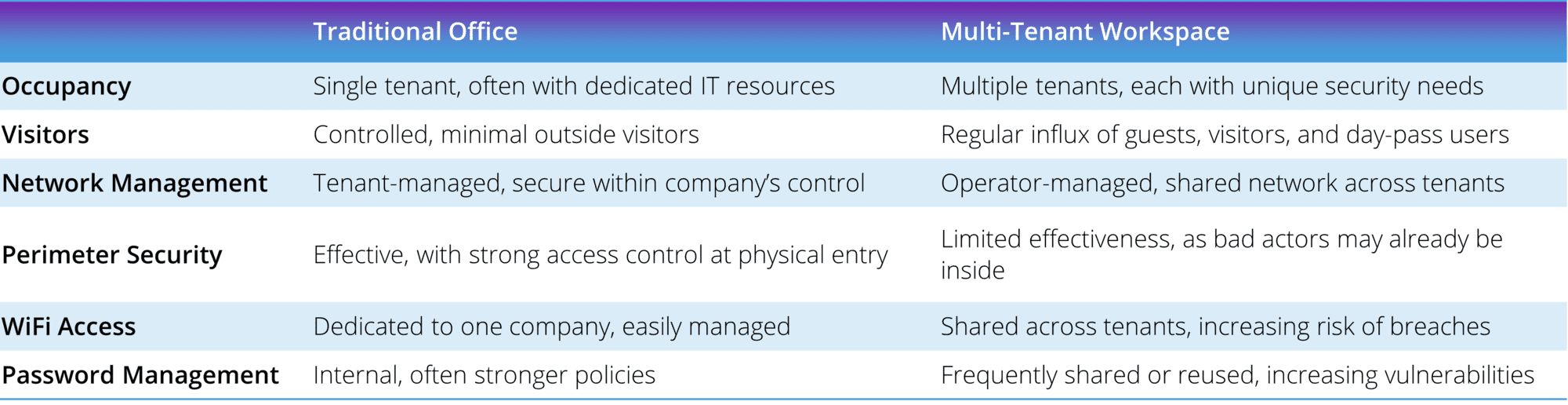
In a traditional office, the security focus was primarily at the perimeter—keeping outsiders from entering the building or gaining access to the network. But in a multi-tenant space, that perimeter has effectively dissolved. Tenants, visitors, contractors, and temporary users are all inside, and they’re often connected to the same network.
Why traditional security measures fall short
For years, CRE operators relied on securing physical entry points, like doors, elevators, and parking garages. These methods worked well for keeping intruders out. But today, the threats aren’t limited to someone walking into the building—they could be sitting next to you, logging into the same shared network.
Relying on shared passwords or simple WPA-2 WiFi protection isn’t enough. Passwords are easily compromised—especially when many tenants and visitors are using the same network, passing credentials around, or reusing weak passwords across different devices. Once a bad actor gets in, they can potentially access sensitive data from multiple businesses on the network.
Additionally, day-pass members and visitors can introduce unknown risks. These individuals often connect personal devices that may not comply with corporate security policies, and in some cases, those devices could already be compromised. Without the right network controls, bad actors can easily exploit these gaps.
The critical role of cybersecurity in multi-tenant workspaces
In this new environment, the responsibility of securing the network rests on your shoulders as the workspace operator. It’s a crucial part of the digital experience (and therefore the overall customer experience) that you’re delivering to your users. It’s critical that you provide a safe and secure digital environment for your users.
This means adopting more advanced cybersecurity measures:
– With certificate-based authentication (EAP-TLS) on top of WPA-2 Enterprise, each device or user is issued a unique digital certificate. This removes the need for usernames & passwords, ensuring the identity is much harder to impersonate. This method is more secure because certificates can’t easily be stolen, guessed, or shared.
– Certificates allow for more granular control, enabling the network to differentiate between different types of users (e.g., employees, guests, contractors) and apply appropriate access rules.
– Certificates are tied to authorized devices, ensuring that even if a user brings a different device, only their trusted device(s) can access secure resources.
– WPA-2 Enterprise with RADIUS provides centralized logging and monitoring of all network authentication attempts, allowing administrators to detect suspicious behavior (e.g., failed login attempts) and respond quickly to potential breaches.
– WPA-2 Enterprise with strong authentication (like certificates) ensures compliance with many security frameworks by providing robust, traceable, and auditable access controls – meaning you’re able to accommodate the requirements of enterprise tenants.
Ultimately, all of this means that the only users (and devices) that can access your network, are those who should be able to do so.
Why it matters now
As a CRE landlord or flexible workspace provider, your reputation is on the line. Tenants expect that not only will their workspace needs be met, but that their digital environment will be just as safe and secure as their physical one. Failing to prioritize cybersecurity could lead to breaches that affect multiple businesses, damaging your credibility and putting tenants’ data at risk.
On top of this, you’re less likely to attract enterprise tenants – those with more stringent security and compliance requirements. If you don’t offer sufficient security measures, they’ll look further down the road for a workspace that does.
Securing the future of flexible workspaces
As the world of work becomes increasingly flexible and shared spaces continue to grow in popularity, cybersecurity must be top of mind for workspace operators. Traditional office security models are no longer enough, and shared networks introduce unique risks that require more advanced, scalable solutions. By embracing best-in-class cybersecurity practices – such as WPA-2 Enterprise and certificate-based authentication – you not only protect your tenants, but you also future-proof your business against the evolving threat landscape.
You’ll likely even see the results in your bottom-line, too.